 Featured at YouTube this
multi-user accounting application is designed to simplify everyday tasks for different industries,
runs on all modern browsers of any operating system in any modern computer or device, delivers
flexible and powerful reports and extensive history in many configurations, links to sturdy user
data, and does not require installations or application updates by the client.
Written in C#® the ASP.NET web based application retains and enhances most aspects of its
Windows® predecessor, including type of business, dynamic menu inclusion, global and user
search and report parameter recall and most other company preferences, as well as productivity
and esthetics. It adds compatibility, mobility, a complete Bill of Materials module,
additional reports, report incidence searches and dynamic control breaks and drill down,
regardless of the user's modern computer or device. In most search grids
the user would dedicate valuable time for the specific filter/sort/paging, advance to the
results window, and for the same session eventually return to the same filter, sort, paging
and record, thus continuing the current task just where it was left off, which is a hard to
find all inclusive time saving option. Given your feedback, our analysis, recommendations,
guidance, database improvements and user cooperation the chances for potential growth and
expansion are increased, and great satisfaction is achieved.
Featured at YouTube this
multi-user accounting application is designed to simplify everyday tasks for different industries,
runs on all modern browsers of any operating system in any modern computer or device, delivers
flexible and powerful reports and extensive history in many configurations, links to sturdy user
data, and does not require installations or application updates by the client.
Written in C#® the ASP.NET web based application retains and enhances most aspects of its
Windows® predecessor, including type of business, dynamic menu inclusion, global and user
search and report parameter recall and most other company preferences, as well as productivity
and esthetics. It adds compatibility, mobility, a complete Bill of Materials module,
additional reports, report incidence searches and dynamic control breaks and drill down,
regardless of the user's modern computer or device. In most search grids
the user would dedicate valuable time for the specific filter/sort/paging, advance to the
results window, and for the same session eventually return to the same filter, sort, paging
and record, thus continuing the current task just where it was left off, which is a hard to
find all inclusive time saving option. Given your feedback, our analysis, recommendations,
guidance, database improvements and user cooperation the chances for potential growth and
expansion are increased, and great satisfaction is achieved.
|
 Calling Potential 2026 Users:
Calling Potential 2026 Users:
|
 2026
We take customer calls seriously, engaging in conversation and sharing best practices, historical
information and solutions with a courteous and friendly approach that leads to a wholesome and
rewarding experience, and we will not cut calls short, or intimidate in any way, for we were
there before, when help was needed and we got a hand.
2026
We take customer calls seriously, engaging in conversation and sharing best practices, historical
information and solutions with a courteous and friendly approach that leads to a wholesome and
rewarding experience, and we will not cut calls short, or intimidate in any way, for we were
there before, when help was needed and we got a hand.
Show us your application and database history, covering areas that may need attention, and which
items fell short of your expectation, or failed along the way, and through our many years worth
of experience and solution delivery in multiple business environments we can cover specific
details in order to determine possible database or procedural repair or improvement, and to
analyze the path to a robust, dynamic and lasting solution that you would be most satisfied with.
Our organization was launched in 1985, providing our multi-user business accounting software with
corresponding database to municipalities, manufacturing, production, retail, pickup & delivery
and other industries, which ran on operating systems Unix, Windows for Workgroups in 1994, then
all the Windows versions up to the 2026 latest, and eventually covering
all modern operating systems in a web based multi-user business accounting interface that was
completed by 2016. We created non-accounting applications for Windows on 2013, such as
our feature rich image viewer/comparison, and our image generating/cataloging package. Our
applications are also featured at YouTube.
|
 Flow Diagram and more details:
Flow Diagram and more details:
|
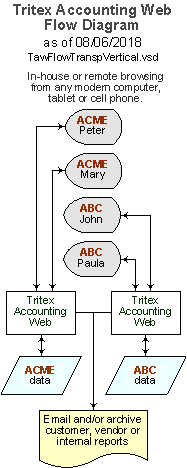 The adjacent diagram illustrates the application and data flow, where the only
requirements are to fine tune your new SQL Server database to populate it with your information,
starting with multiple look-up tables, followed by the determined level of detail, whether or
not a data conversion effort is involved. If you choose to host the data it would require
additional periodic certification as well as at least a 2016 or newer version of SQL Server™
or the free SQL Server Express™ environment. In this example four users in two
separate organizations are connecting to our application servers, which securely route them
to the corresponding secure data, while reports are also archived at their location through
their designated no-reply email account, or through our simplified export to PDF feature.
The application security employs a strongly encrypted Secure Socket Layer connection, and Windows
authentication to prevent anonymous access. The login process includes a captcha image, which
text cannot be captured, a strong company password, the company's user password, and an optional
authentication code, that is texted to the login user to help prevent breaching efforts.
Your data provides a configurable login user name and password, and company and user preferences
then determine which menu items are omitted from the specific user, or which items are
partially or fully available to the user, such as read-only Chart of Accounts or limited
company maintenance. When the first license is purchased your Company Name and
User ID are provided to us and we randomize a Company Code for you to login. When
follow up licenses are purchased just the new User ID is provided to us. When
resetting a user password, or removing a user from your database we expect the details
from you in order to sync to our application servers. Also you can have us reset
the company code at any time, especially after you change personnel. Please reference
the below bulleted security measures.
The adjacent diagram illustrates the application and data flow, where the only
requirements are to fine tune your new SQL Server database to populate it with your information,
starting with multiple look-up tables, followed by the determined level of detail, whether or
not a data conversion effort is involved. If you choose to host the data it would require
additional periodic certification as well as at least a 2016 or newer version of SQL Server™
or the free SQL Server Express™ environment. In this example four users in two
separate organizations are connecting to our application servers, which securely route them
to the corresponding secure data, while reports are also archived at their location through
their designated no-reply email account, or through our simplified export to PDF feature.
The application security employs a strongly encrypted Secure Socket Layer connection, and Windows
authentication to prevent anonymous access. The login process includes a captcha image, which
text cannot be captured, a strong company password, the company's user password, and an optional
authentication code, that is texted to the login user to help prevent breaching efforts.
Your data provides a configurable login user name and password, and company and user preferences
then determine which menu items are omitted from the specific user, or which items are
partially or fully available to the user, such as read-only Chart of Accounts or limited
company maintenance. When the first license is purchased your Company Name and
User ID are provided to us and we randomize a Company Code for you to login. When
follow up licenses are purchased just the new User ID is provided to us. When
resetting a user password, or removing a user from your database we expect the details
from you in order to sync to our application servers. Also you can have us reset
the company code at any time, especially after you change personnel. Please reference
the below bulleted security measures.
We fully enforce referential integrity throughout a vast number of objects in the robust
SQL Server™ database, thus helping prevent data related errors or loss. We
then assist in populating this performance driven database. The affordable multi-user
application provides powerful reports, which recall global and user parameters, including
search and variable control breaks and drill down, even if run from a cell phone.
Its seamless email of sales invoice or quote, customer statement, late notice and
purchase order also copy you through a company designated email account, thus minimizing
on paper use. Its ability to upload salesperson and product images, and general
reporting graphical messages or logos to the company table conform to its predecessor
Windows application, but can now be done from a cell phone. And its purchase order
and inventory control sub-systems enforce quantity on hand, whether you work remotely or
from the office, with the optional non-use of QOH in your company preferences.
Purchase Order entry automatically logs up to 3 price changes per
vendor/product, and new line item entries automatically recall the last price for the
current vendor/product. Any P/O price adjustment will archive the last price for
that vendor/product, rotating the 3 prices, while losing the oldest one. Sales Order
entry recalls pricing methods that are based on a customer's look-up of special sales price
by date, hourly rate, price code level per customer/product (namely RepBillPrice), customer
price level code by percent over last-cost-in/average-cost/inventory-price (least
maintenance but level is not by product), or prices straight off of the inventory code
per unit of measure or per each, whichever sales order entry automatically finds first.
Therefore the proper and precise setup can lead to a rewarding return, and to a great and
proficient model for your ongoing maintenance.
Also a Bill of Materials (BOM) feature is included in Inventory Control, which
provides very useful job costing routines, including forecasted material requirements,
which sub-system is featured in the above BOM tab, and also at
YouTube.
Our closing routines specify the needed reports and controls previous to the closing step,
and in addition ask again before the user begins the closing. If a user disregards
these warnings and damages the data at year's end a restoration of the database is in order
to prevent the loss of sales comparisons between years, whether by Customer, Product or
Salesperson. Or should a user close the year more than once then the year comparisons
get rolled over into oblivion and get lost. If unsure whether you already closed then
attempt to obtain the control report, and if it is empty then you have already closed.
For periodic or monthly closings the user should obtain the final and full printout
or export to PDF previous to initializing the period, which should be performed only
once for that period.
By allowing the initial setup of only customer billing aspects and inventory code the
application provides a fast implementation of your Sales Order, Invoicing, Accounts Receivable,
Cash Receipts and Inventory Control, which quantity on hand is also optional. You may then
incorporate the other sub-systems, or you may include them at the beginning, while
the full-fledged application provides purchase order, inventory control, pricing analysis/strategy,
pricing methods as specified above, accounts payable, accounts payable disbursements,
manufacturing, bill of materials, wholesale, distributor, retail and service preferences,
sales order, order status, customer quotes, customer invoice, accounts receivable,
cash receipts, multiple payments, partial payments, cash discounts, sales discounts,
salesman commission, chart of accounts, general ledger, financial reports, and your
ability to provide suggestions for the application, which we take seriously.
The application comes with all of the above options, whether some are used or not.
Should the data files be hosted by us then we handle SQL Server, backup and security, otherwise
if you host them then the following applies: Any data upgrades do require our secure access
to keep them in sync and up to date, and you should regularly backup your database,
while we can guide you in learning backup/restore procedures. If you are new to
SQL Server we can also guide you in obtaining, installing and maintaining its latest
version, where SQL Server Express is a free product, which limitations might not affect
you, such as over 2 billion objects, over 16 terabytes of data file size, and over
2 terabytes of log file size, while the simple recovery model keeps the log file size down,
and requires less maintenance. Over the long haul you gain valuable experience in this
environment, while we assist you with performance aspects, such as utilizing table index
optimization in lieu of database shrinking. Regardless of the database host we encourage
not bypassing the application interface.
Please compare our pricing to the monthly costs of engaging a database in another environment,
where you perform, or forget to perform backup procedures yourself, where the database does not
sync to a web based and fully integrated accounting application that is self upgraded, where
guidance and support does not compare to ours, where any additional field or table may or may
not be needed to accomplish a possible enhancement, and you get stuck with using one too many
user-defined fields, and where it is left up to you not to build up so much redundancy in the
database, that there is no point of return left open, with poor guarantee of performance and
excessive maintenance through the years to come. Come with us and concentrate on your
business, with greater chances of expansion.
 As your business progresses you may find the need to expand and enhance your procedures, and
rather than conforming to partial solutions and limited user defined fields you may realize
that we are there to truly help you attain sustained, robust and dynamic solutions.
Collaboration might yield existing options that you had not yet tapped unto, that may
simply require populating an existing look up table to further incorporate it into your logic,
or implementing a system preference that would turn on features which you did not know you had
access to. Or there may be a time saving option that you were not aware of, such as
services at customer hourly rates, which calculate hours based on date/time ranges, and automatic
assignment of these time calculations to quantity ordered for your service order or quote.
And should the request for a new feature represent a potential improvement to the application
we can consider and implement it based on system preferences. We would enjoy discussing
a history of issues that you may have had in the past, and would share our feed back, whether
you have solved or circumvented them, and usually things turn out very good. Given our
dedication to enhance your business, this application's capabilities, your engagement, and
a sustained win-win approach, you grow with us, and we grow with you.
As your business progresses you may find the need to expand and enhance your procedures, and
rather than conforming to partial solutions and limited user defined fields you may realize
that we are there to truly help you attain sustained, robust and dynamic solutions.
Collaboration might yield existing options that you had not yet tapped unto, that may
simply require populating an existing look up table to further incorporate it into your logic,
or implementing a system preference that would turn on features which you did not know you had
access to. Or there may be a time saving option that you were not aware of, such as
services at customer hourly rates, which calculate hours based on date/time ranges, and automatic
assignment of these time calculations to quantity ordered for your service order or quote.
And should the request for a new feature represent a potential improvement to the application
we can consider and implement it based on system preferences. We would enjoy discussing
a history of issues that you may have had in the past, and would share our feed back, whether
you have solved or circumvented them, and usually things turn out very good. Given our
dedication to enhance your business, this application's capabilities, your engagement, and
a sustained win-win approach, you grow with us, and we grow with you.
New accounts start out with a predefined Chart of Accounts and basic look up information,
while the actual salesperson, vendor, terms, types and other look up data, as well as system
preferences, users and user permission are initially analyzed and setup. Once look up
information is setup the Company and Preference settings are further tuned up for your
specific industry, the actual customers and vendors are then entered, while their look up
information is already in place. Next are the current transactions, their status
and balances, and history. Then the Chart of Accounts is tuned up to match your
accounts, with further tuning after enough data is available to run reports. We help you
achieve a successful implementation, assisting with the initial data entry and setup, and
determining the flavor of SQL Server to hold your database, should you host it. We
also specialize in converting your data from other sources to SQL Server, and for a
fair fee will step through look up tables, customers, vendors, current transactions,
and even history in the process of incorporating your new database. Since we apply
referential integrity to your data it might be necessary to adjust look up information
such as a missing salespeople, duplicate account numbers, or leftover accounts and codes,
where we would need your cooperation in order to retain valid history. Once a database
is up to par it is nearly impossible to break it, however, to stay away from redundancy,
duplication or orphaning issues, and to simplify maintenance please consult us previous to
implementing data or procedural solutions. For instance, substantial changes to accounts
or pricing method might generate different results when shipped quantity changes are applied
to previous transactions, where consulting us might result in retaining your data
intact. In cases where a separate account must be created, consult us for the proper
balance transfer, with a possible account status change.
In view of the advantages of running any part of the application
remotely from a computer, laptop, tablet or cell phone, and with your
security taking precedence we have incorporated a
web session timeout of 600 minutes after each login, and an
inactivity timeout of 60 minutes, which is a long enough
time for security and compliance related reasons. For instance, going to lunch means
logging out of the application. Regardless of the reason for closing the browser
without first logging out we have permitted the same users to login again, even if the
system still considers them to already be logged in, however, if for some reason the
user was still physically logged into the application then that earlier session will
encounter a warning with automatic logout upon any navigation performed, as each
license constitutes a user at a time. Therefore save any changes previous to
attempting to perform another same-user login concurrently. In essence, just
save your changes as often as possible. Please be aware that the improvement to
run the company remotely from a PC or device requires added security and compliance
measures to be followed.
|
 Security recommendations:
Security recommendations:
|
-
Any computer or laptop to be used to run this application should regularly apply the latest
security updates. Computers, laptops, tablets and cell phones should either be
dedicated to the application, or their users should become security savvy, and well-informed
and perceptive about not disclosing your data on some social network by enforcing as much
privacy as possible on their profiles, about never saving passwords, never lending your
computer or device if it is intended to run this application, and generally in protecting
the database, as if it were your own health.
-
Even though our servers employ highly encrypted SSL connections we recommend the use of
your own PC, laptop, tablet or cell phone, rather than a shared or borrowed computer or
device at a public hotspot or relative's house. If on a public hotspot and you need
to login to the application then use your own data plan to connect for the smaller duration
of time, rather than their public Wi-Fi. And note that your device could get pried
upon while on the Wi-Fi, and then when switching to your plan's connection it might already
be in trouble, remember about the existence of key loggers that steal your passwords.
That is the reason for dedicating devices to the application.
-
For a home Wi-Fi connection make sure that the highest available security protocol employs a
strong password, otherwise third parties or neighbors could attempt to unencrypt the packets
to get to your data. WEP and WPA are the lowest denominators, and easy to crack
protocols, followed by WPA2 and then WPA3, where the minimum recommended is WPA2 using a
pretty strong user password in lieu of the factory password. WPA3 is available,
but since it was built backwards compatible with WPA2 based on outdated remote equipment
even WPA3 could compromise your Wi-Fi password. Also in some cases WPA3 fails in
certain routers with very low performance when hosting videos in a Windows server,
and only time will correct these issues vendors are having. In conclusion, whether
on WPA2 or WPA3 always change the router factory's to a strong user Wi-Fi password.
A Wi-Fi connection without appropriate security is a grave mistake, even if our application
additionally encrypts communications with the user. If possible
use ethernet cables in lieu of Wi-Fi. Also get used to clearing your browser cache,
cookies and related data after every use, and specifically just learn how to do it.
And never leave the workplace without having logged out from the application, cleared
the browser cache, closed the browser and locked the computer or device, even if you
think you'll be alone. If you will certainly be alone then any inactivity over
60 minutes will automatically log you off, but not
lock your screen, therefore always setup screens to timeout with a lock, and always require
a password to unlock a PC or device. Note that even when no harm is intended a shared
home computer or device should never be used to run this application. Please train
all of your personnel to avoid use of the browser back button or typing into the URL window,
as it will certainly get trapped by the application at certain navigation spots, and you
might lose recent entries. For instance user 1 logs off and takes a break, user 2
presses the back button to enter your login state, but this application will trap that
move. Or user 1 logs off of the application and additionally closes the browser,
and then user 2 attempts to browse into a specific application URL path they saw before,
but the application traps that as well. Of course, there are instances where login
state did not change, and the back arrow would then work, but you might lose changes
that were not yet saved, or cause a previous operation to be repeated. As a rule
of thumb navigate only through the application's interface, and never leave it unattended.
-
Never use a computer or device to run this application if there is a possibility of
intrusion due to noticeable performance degradation, or to a known incident that could
be suspected to be virus or spam, even if not that malicious. Be aware that
many tools that claim to clean up your software might be compromised themselves.
Once infected only a computer drive format or device reset and reinstall of all safe
apps are about the only safe way out. Better yet, a good image backup is the
fastest and easiest recovery, while this applies to the Windows operating system.
Please consult your device vendor to
insure that you can retain all of your contacts and other information previous to
a device reset. Keep this rule of thumb all the time: A PC or device
intended to run this application should almost be dedicated to it, and questionable
internet browsing, emailing or texting should usually be performed with other machines
or devices. Any sign of performance degradation could be a sign of intrusion,
and it is better to be safe than sorry. Email messages that are sent to or
received from multiple recipients are more apt to be infected due to the volume.
Open email attachments only if you feel that senders are not infected victims
themselves, and that they are not being impersonated.
|